Unified Cyber Risk Management
Your AI Teammates for Continuous Threat & Exposure Management
Your AI Teammates for Continuous Threat & Exposure Mgmt.
From zero-day detection to automated investigations and proactive exploitability management—our AI-native Cyber Mesh keeps your teams ahead.
From zero-days to auto-resolution—stay ahead with AI-native security.


MaayaAI solves
The Biggest Problem in Cybersecurity Today
The biggest problem in cybersecurity today
MaayaAI delivers the only native GenAI mesh platform for vulnerability management, combining fine-tuned LLMs, proprietary AI-native Cyber Mesh technology, and agentic automation.
MaayaAI delivers the only native GenAI mesh platform for vulnerability management, combining fine-tuned LLMs, proprietary AI-native Cyber Mesh technology, and agentic automation.
Autonomous AI Agents
Automate complex vulnerability workflows for fully autonomous assessments.
Autonomous AI Agents
Automate complex vulnerability workflows for fully autonomous assessments.
Schema-less Platform
Greater flexibility, scalability, and effectiveness in handling diverse datasets.
Schema-less Platform
Greater flexibility, scalability, and effectiveness in handling diverse datasets.
AI Teammates
Ultimate blend of speed, collaboration, adaptability, and proactive engagement.
AI Teammates
Ultimate blend of speed, collaboration, adaptability, and proactive engagement.
AI Teammates
Ultimate blend of speed, collaboration, adaptability, and proactive engagement.
Cyber Mesh
Deep, contextual understanding, breaking data silos for instant assessments.
Cyber Mesh
Deep, contextual understanding, breaking data silos for instant assessments.
Cyber Mesh
Deep, contextual understanding, breaking data silos for instant assessments.
Risk Prioritization
Correlates exploitability, asset criticality, and threat signals to surface real risk.
Risk Prioritization
Correlates exploitability, asset criticality, and threat signals to surface real risk.
Risk Prioritization
Correlates exploitability, asset criticality, and threat signals to surface real risk.
Remediation Orchestration
Coordinates fixes across tools and teams, validating remediation and accelerating closure.
Remediation Orchestration
Coordinates fixes across tools and teams, validating remediation and accelerating closure.
Achievements and conferences
Achievements and conferences
We engage with the community through leading conferences and key industry forums.
We engage with the community through leading conferences and key industry forums.
What MaayaAI brings to the battlefield
Drowning in data and rising threats? AI-driven attacks make automated security workflows essential for risk and compliance.
What MaayaAI brings to the battlefield
Drowning in data and rising threats? AI-driven attacks make automated security workflows essential for risk and compliance.
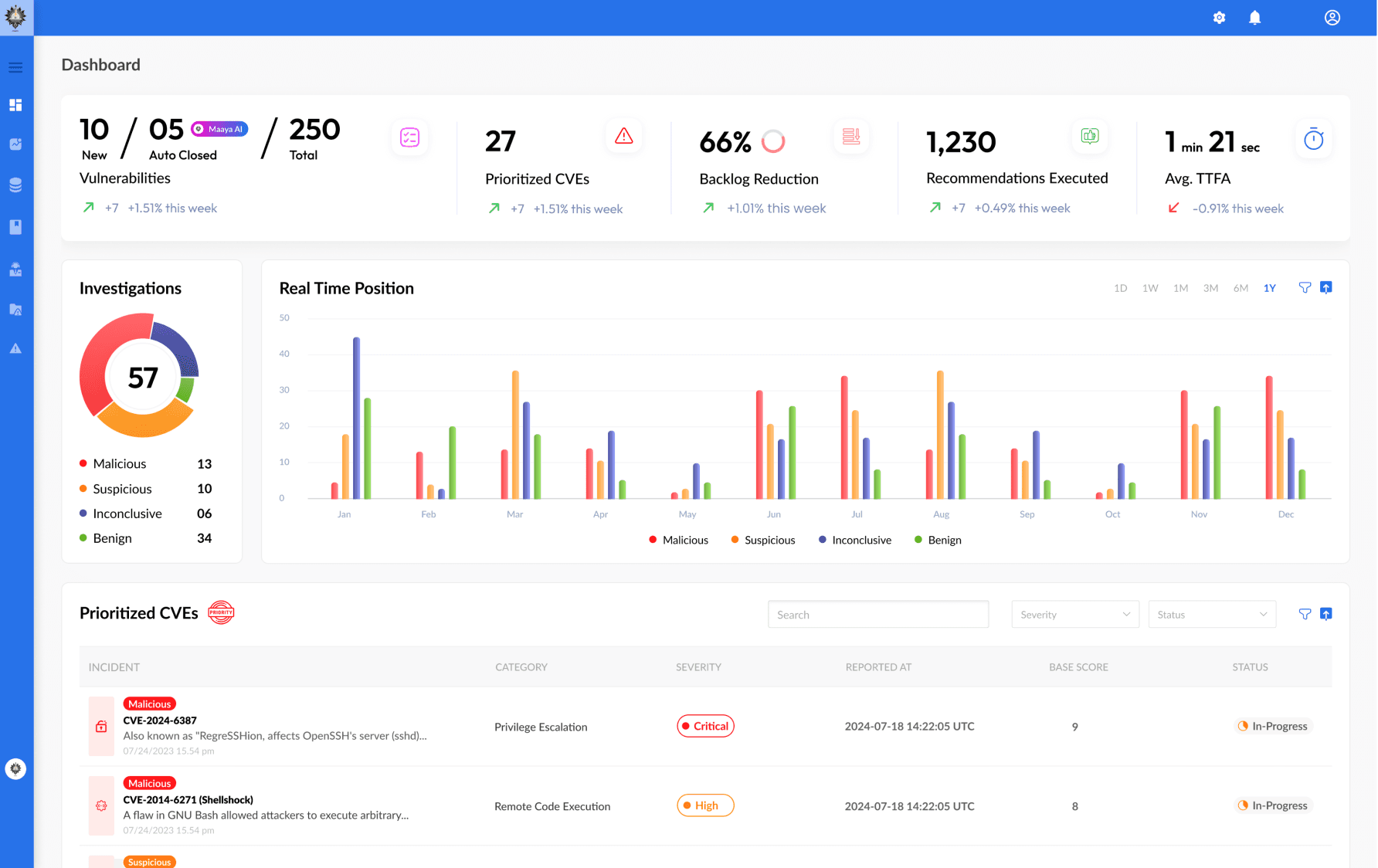
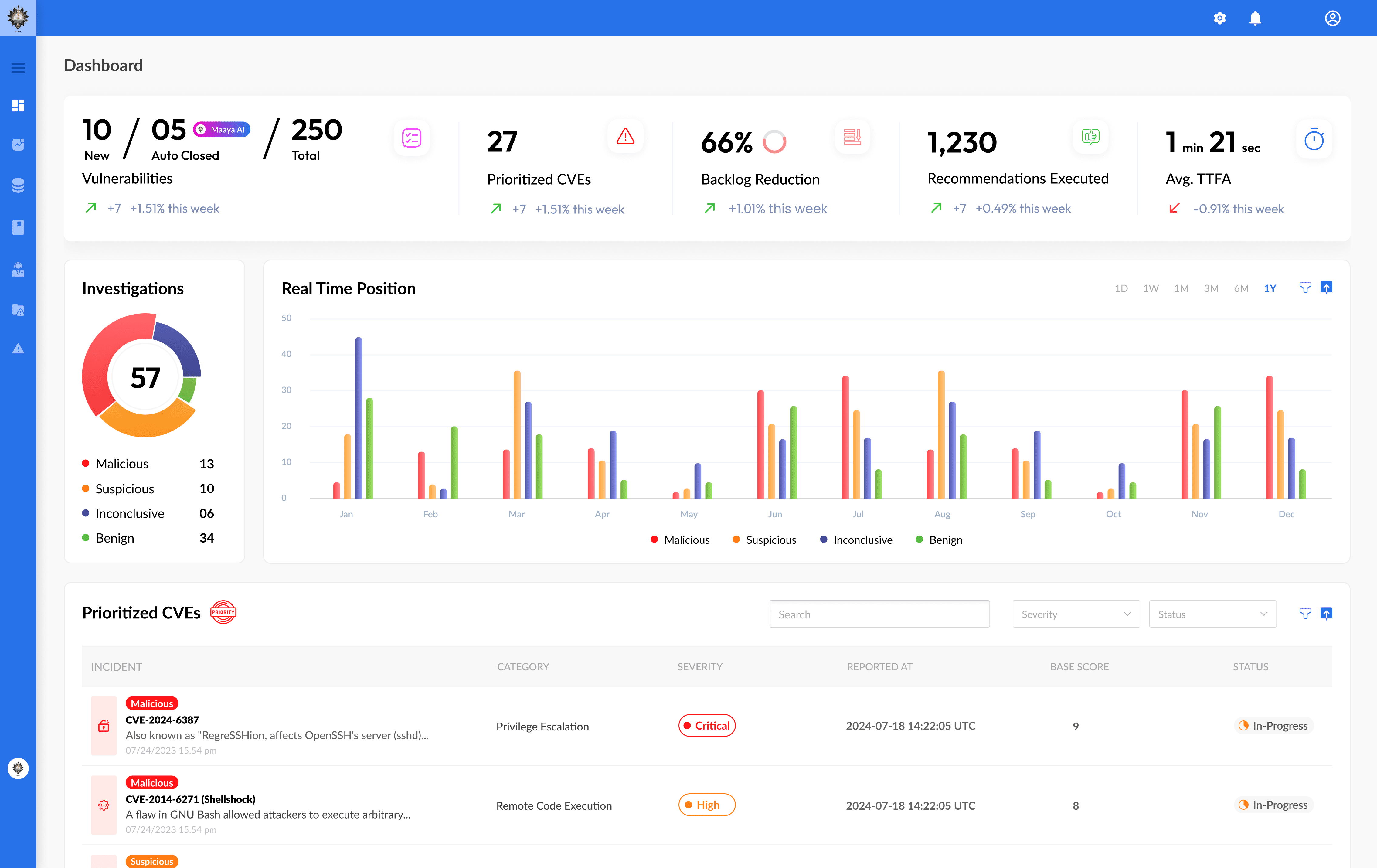
Instant 0-Day Risk & Impact Assessment
Go from alert to insight in seconds. MaayaAI identifies critical vulnerabilities before they become real threats.
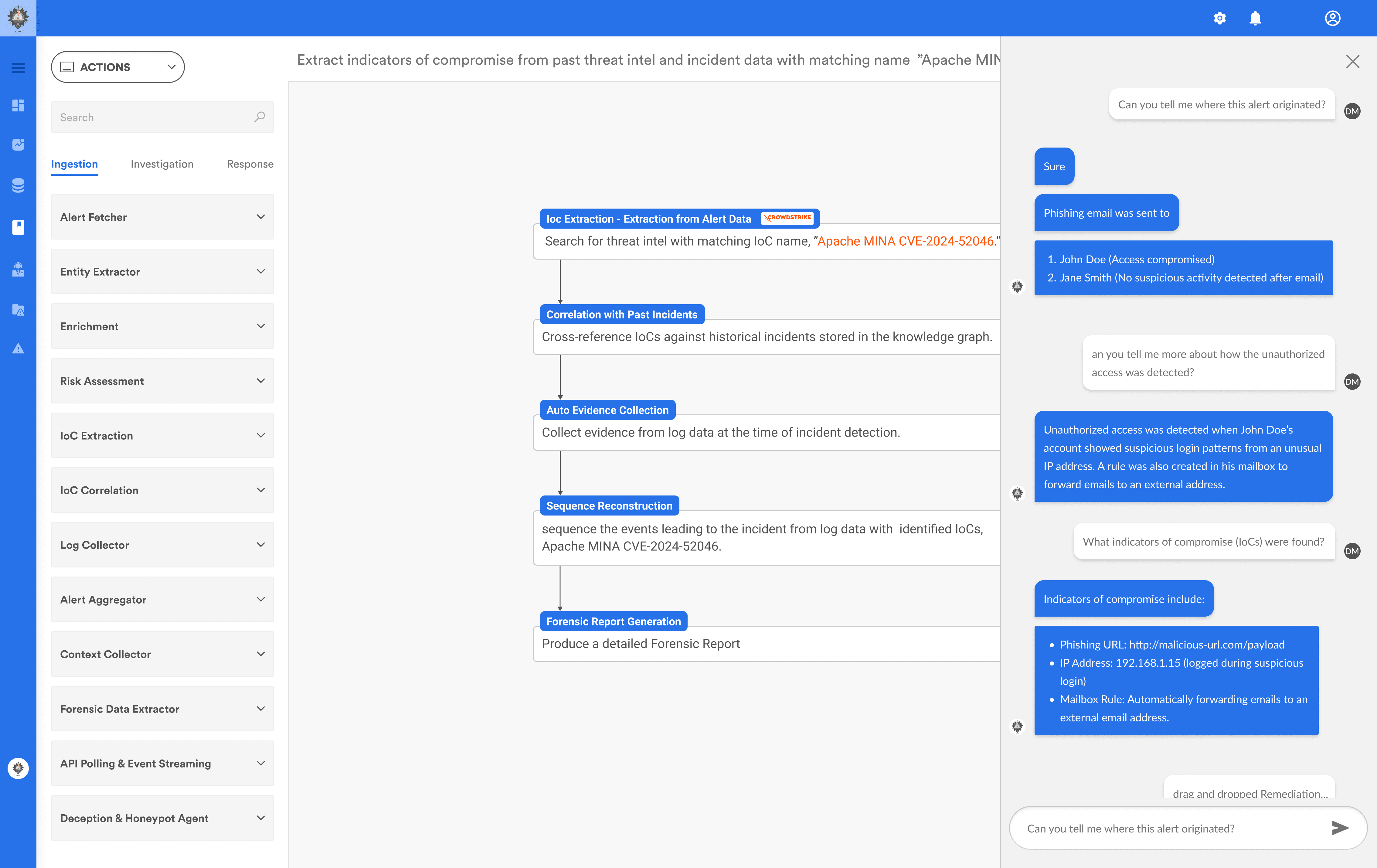
Autonomous + AI-Guided Investigations
Minimize manual work. Let AI assist, guide, and resolve complex threat chains with unmatched accuracy.
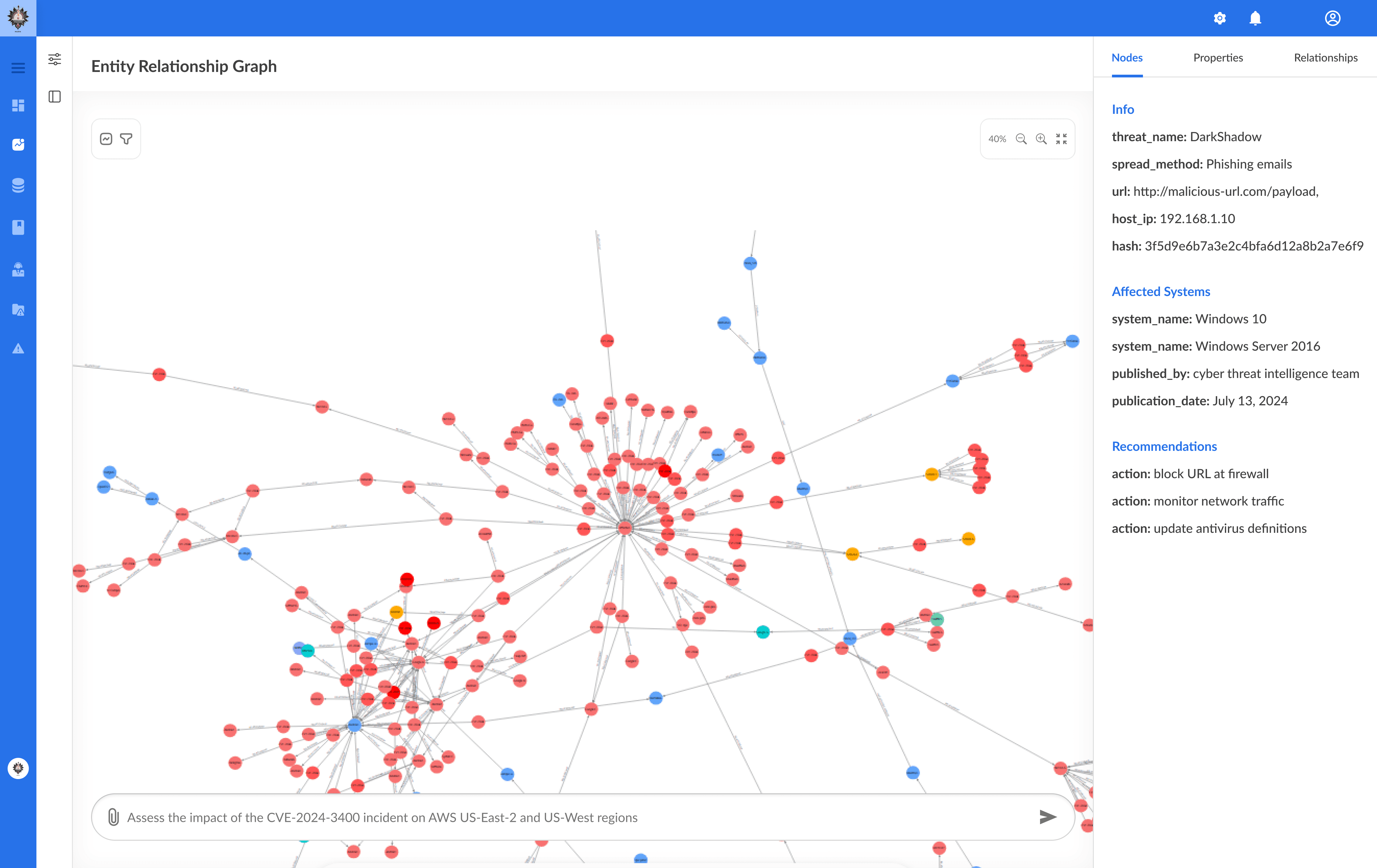
Cyber Mesh-Powered Intelligence
Unify and correlate data across silos. See the full picture with graph-driven insights.
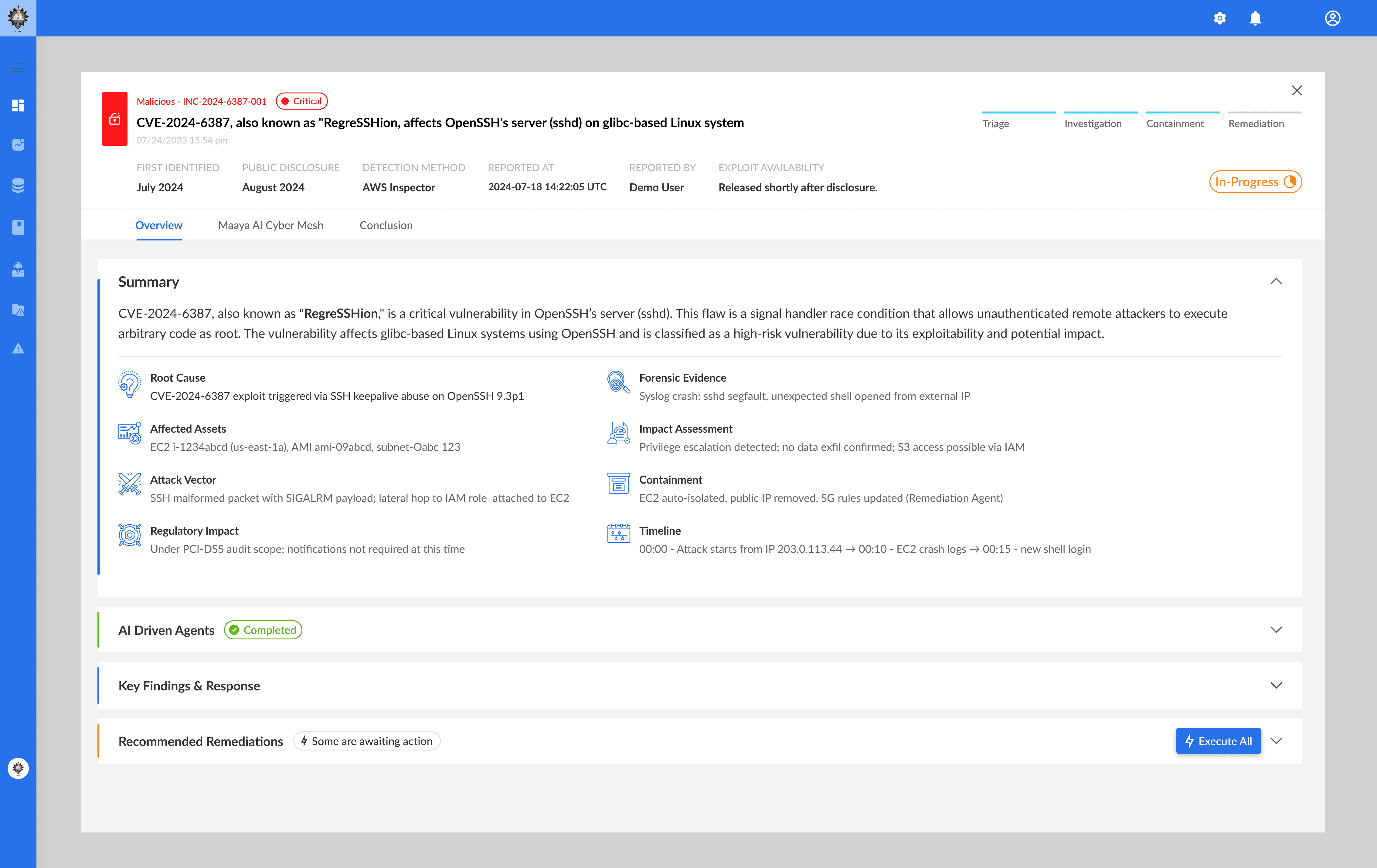
Agent-Led Remediation
Take instant action. Auto-convert insights into policies across SIEMs, WAFs, EDRs, and NDRs.

Instant 0-Day Risk & Impact Assessment
Go from alert to insight in seconds. MaayaAI identifies critical vulnerabilities before they become real threats.

Instant 0-Day Risk & Impact Assessment
Go from alert to insight in seconds. MaayaAI identifies critical vulnerabilities before they become real threats.

Autonomous + AI-Guided Investigations
Minimize manual work. Let AI assist, guide, and resolve complex threat chains with unmatched accuracy.

Autonomous + AI-Guided Investigations
Minimize manual work. Let AI assist, guide, and resolve complex threat chains with unmatched accuracy.

Cyber Mesh-Powered Intelligence
Unify and correlate data across silos. See the full picture with graph-driven insights.

Cyber Mesh-Powered Intelligence
Unify and correlate data across silos. See the full picture with graph-driven insights.

Agent-Led Remediation
Take instant action. Auto-convert insights into policies across SIEMs, WAFs, EDRs, and NDRs.

Agent-Led Remediation
Take instant action. Auto-convert insights into policies across SIEMs, WAFs, EDRs, and NDRs.
MaayaAI platform can reduce upto 70%
time and cost of security operations
MaayaAI platform can reduce upto 70%
time and cost of security operations
MaayaAI platform can reduce upto 70%
time and cost of security operations
Dominate, Revolutionize
Your Cyber Defense
Dominate, Revolutionize
Your Cyber Defense

Automated Security Controls
Adopt proactive defense by tuning controls based on exploitability, integrating data to reduce drift, optimize performance, and strengthen security posture.

Automated Security Controls
Adopt proactive defense by tuning controls based on exploitability, integrating data to reduce drift, optimize performance, and strengthen security posture.

Automated Security Controls
Adopt proactive defense by tuning controls based on exploitability, integrating data to reduce drift, optimize performance, and strengthen security posture.
Automation using Agents
Agentic architecture maps posture gaps to real-time data, converting insights into policies across SIEMs, WAFs, EDRs, and NDRs.

Automation using Agents
Agentic architecture maps posture gaps to real-time data, converting insights into policies across SIEMs, WAFs, EDRs, and NDRs.

Automation using Agents
Agentic architecture maps posture gaps to real-time data, converting insights into policies across SIEMs, WAFs, EDRs, and NDRs.

Risk Mitigation
Dynamically map vulnerabilities with exploit validation, config analysis, and attack path insights via NLP-driven graphs, prioritizing real, actionable threats.

Risk Mitigation
Dynamically map vulnerabilities with exploit validation, config analysis, and attack path insights via NLP-driven graphs, prioritizing real, actionable threats.

Risk Mitigation
Dynamically map vulnerabilities with exploit validation, config analysis, and attack path insights via NLP-driven graphs, prioritizing real, actionable threats.

Real Time Knowledge
Instantly aggregate diverse data — advisories, vulnerabilities, internal docs, compliance drafts, and incidents — with proprietary, fine-tuned models.

Real Time Knowledge
Instantly aggregate diverse data — advisories, vulnerabilities, internal docs, compliance drafts, and incidents — with proprietary, fine-tuned models.

Real Time Knowledge
Instantly aggregate diverse data — advisories, vulnerabilities, internal docs, compliance drafts, and incidents — with proprietary, fine-tuned models.
Why MaayaAI
Real risk. Real action. Powered by GenAI.
Real risk. Real action. Powered by GenAI.
Other Tools
Only raise alerts, require manual triage
Rely on generic scores (e.g., CVSS) and noise
Static dashboards; no autonomous actions
Offer guidance only; ops must act separately
Periodic or manual rescans; no adaptive loop

MaayaAI
Investigates and resolves risks automatically
Ranks by business impact and attack paths
AI powered investigation & remediation
Pushes fixes to Jira/CMDB/IaC/CD pipelines
Re-evaluates post-fix risk & surface changes
Other Tools
Only raise alerts, require manual triage
Rely on generic scores (e.g., CVSS) and noise
Static dashboards; no autonomous actions
Offer guidance only; ops must act separately
Periodic or manual rescans; no adaptive loop

MaayaAI
Investigates and resolves risks automatically
Ranks by business impact and attack paths
AI powered investigation & remediation
Pushes fixes to Jira/CMDB/IaC/CD pipelines
Re-evaluates post-fix risk & surface changes
Other Tools
Only raise alerts, require manual triage
Rely on generic scores (e.g., CVSS) and noise
Static dashboards; no autonomous actions
Offer guidance only; ops must act separately
Periodic or manual rescans; no adaptive loop

MaayaAI
Investigates and resolves risks automatically
Ranks by business impact and attack paths
AI powered investigation & remediation
Pushes fixes to Jira/CMDB/IaC/CD pipelines
Re-evaluates post-fix risk & surface changes
MaayaAI unifies security data with fine-tuned LLMs and SLMs. Pinpointing real risk and automating mitigation at scale. Delivering continuous, compliant security outcomes.
MaayaAI unifies security data with fine-tuned LLMs and SLMs. Pinpointing real risk and automating mitigation at scale. Delivering continuous, compliant security outcomes.
Got questions?
We’ve got answers.
Here’s everything you need to know before getting started.
Got questions?
We’ve got answers.
Here’s everything you need to know before getting started.
01
How does MaayaAI decide what is truly critical?
MaayaAI analyzes exploitability, asset exposure, attack paths, and blast radius to rank vulnerabilities by material impact, not theoretical severity.
02
Will MaayaAI work with my existing security tools?
Yes. MaayaAI seamlessly integrates with scanners, SIEM, cloud, endpoint, identity, and ticketing tools—maximizing your current investments without rip-and-replace.
03
Does MaayaAI replace my security analysts?
No. MaayaAI acts as an AI teammate, handling L2/L3 investigations and forensics so analysts can focus on decisions, strategy, and response—not manual triage.
04
How fast can MaayaAI assess and respond to a threat?
MaayaAI reduces investigations from weeks to minutes by automating validation, impact analysis, evidence collection, and remediation recommendations.
05
What happens after a vulnerability is fixed?
Unlike periodic rescans, MaayaAI continuously re-evaluates the environment, ensuring the risk is truly eliminated and no new attack paths emerge.
06
How can I get support if I run into issues?
We’re here to help. If you have questions, you can reach us directly at support@maayaai.com. We usually respond within 24 hours.
01
How does MaayaAI decide what is truly critical?
MaayaAI analyzes exploitability, asset exposure, attack paths, and blast radius to rank vulnerabilities by material impact, not theoretical severity.
02
Will MaayaAI work with my existing security tools?
Yes. MaayaAI seamlessly integrates with scanners, SIEM, cloud, endpoint, identity, and ticketing tools—maximizing your current investments without rip-and-replace.
03
Does MaayaAI replace my security analysts?
No. MaayaAI acts as an AI teammate, handling L2/L3 investigations and forensics so analysts can focus on decisions, strategy, and response—not manual triage.
04
How fast can MaayaAI assess and respond to a threat?
MaayaAI reduces investigations from weeks to minutes by automating validation, impact analysis, evidence collection, and remediation recommendations.
05
What happens after a vulnerability is fixed?
Unlike periodic rescans, MaayaAI continuously re-evaluates the environment, ensuring the risk is truly eliminated and no new attack paths emerge.
06
How can I get support if I run into issues?
We’re here to help. If you have questions, you can reach us directly at support@maayaai.com. We usually respond within 24 hours.
01
How does MaayaAI decide what is truly critical?
MaayaAI analyzes exploitability, asset exposure, attack paths, and blast radius to rank vulnerabilities by material impact, not theoretical severity.
02
Will MaayaAI work with my existing security tools?
Yes. MaayaAI seamlessly integrates with scanners, SIEM, cloud, endpoint, identity, and ticketing tools—maximizing your current investments without rip-and-replace.
03
Does MaayaAI replace my security analysts?
No. MaayaAI acts as an AI teammate, handling L2/L3 investigations and forensics so analysts can focus on decisions, strategy, and response—not manual triage.
04
How fast can MaayaAI assess and respond to a threat?
MaayaAI reduces investigations from weeks to minutes by automating validation, impact analysis, evidence collection, and remediation recommendations.
05
What happens after a vulnerability is fixed?
Unlike periodic rescans, MaayaAI continuously re-evaluates the environment, ensuring the risk is truly eliminated and no new attack paths emerge.
06
How can I get support if I run into issues?
We’re here to help. If you have questions, you can reach us directly at support@maayaai.com. We usually respond within 24 hours.
Explore the blog
Explore the blog





Validated by Industry Experts
Trusted by seasoned security professionals who understand real risk. Hear directly from them on why MaayaAI delivers impact beyond alerts.
Validated by Industry Experts
Trusted by seasoned security professionals who understand real risk. Hear directly from them on why MaayaAI delivers impact beyond alerts.
"I like your approach to (Cybersecurity Mesh Architecture), open, multi-vendor platform. Other platforms are not really doing this. I wish the security vendors could cooperate more."
Patrick Hevesi VP Analyst, Gartner (GPT & CMSA Lead)
"I like MaayaAI approach of native AI fabric with LLMs/SLMs addressing the need for both integrations and automation"
Bradley Schaunfenbeul, CISO, Paychex
"If i can squeeze an extra 5-10% of my existing investments I am all up for it"
Vice President Security Operations, Medium Enterprise
"I like your approach to (Cybersecurity Mesh Architecture), open, multi-vendor platform. Other platforms are not really doing this. I wish the security vendors could cooperate more."
Patrick Hevesi VP Analyst, Gartner (GPT & CMSA Lead)
"I like MaayaAI approach of native AI fabric with LLMs/SLMs addressing the need for both integrations and automation"
Bradley Schaunfenbeul, CISO, Paychex
"If i can squeeze an extra 5-10% of my existing investments I am all up for it"
Vice President Security Operations, Medium Enterprise
Contact Us
Write us a message!
Write us a message!
See How Agentic Security Can Transform Your Security Operations
See How Agentic Security Can Transform Your Security Operations




