The Platform
MaayaAI Native AI Security Platform
MaayaAI Native AI Security Platform
The revolutionary Cyber Mesh architecture powered by fine-tuned LLMs/SLMs and proprietary built Security Knowledge Graphs, utilizing a AI native fabric, represents the future of cybersecurity for Info Security Analysts, Digital Forensics, and GRC Teams.
The revolutionary Cyber Mesh architecture powered by fine-tuned LLMs/SLMs and proprietary built Security Knowledge Graphs, utilizing a AI native fabric, represents the future of cybersecurity for Info Security Analysts, Digital Forensics, and GRC Teams.





Integration
Integration
Integration
Built to Work With Your Stack
Built to Work With
Your Stack
MaayaAI platform seamlessly integrates with your existing security ecosystem, maximizing your investments. The platform connects with a wide range of tools to deliver actionable intelligence at scale.
MaayaAI platform seamlessly integrates with your existing security ecosystem, maximizing your investments. The platform connects with a wide range of tools to deliver actionable intelligence at scale.
Vulnerability Scanners




Vulnerability Advisories/Reports/Product/Document/Blogs




Identity



Endpoint


Threat Intelligence





SIEM
One Unified Platform For All Your Security Operations
One Unified Platform For All Your Security Operations
One platform. Total visibility. Faster action.
MaayaAI unifies security operations with AI-driven insights and automation.
One platform. Total visibility. Faster action.
MaayaAI unifies security operations with AI-driven insights and automation.
Digital Forensics
The platform automates evidence collection, log analysis, chain reconstruction, context enrichment from external intel, threat correlation, evidence documentation, and metadata tracking.
Digital Forensics
The platform automates evidence collection, log analysis, chain reconstruction, context enrichment from external intel, threat correlation, evidence documentation, and metadata tracking.
Threat Intel & Vulnerability Teams
Aggregate and contextualize threat intelligence across sources for instant insight. Assess new vulnerabilities fast and resolve them quicker using past learnings.
Threat Intel & Vulnerability Teams
Aggregate and contextualize threat intelligence across sources for instant insight. Assess new vulnerabilities fast and resolve them quicker using past learnings.
Digital Forensics
The platform automates evidence collection, log analysis, chain reconstruction, context enrichment from external intel, threat correlation, evidence documentation, and metadata tracking.
Digital Forensics
The platform automates evidence collection, log analysis, chain reconstruction, context enrichment from external intel, threat correlation, evidence documentation, and metadata tracking.
Threat Intel & Vulnerability Teams
Aggregate and contextualize threat intelligence across sources for instant insight. Assess new vulnerabilities fast and resolve them quicker using past learnings.
Threat Intel & Vulnerability Teams
Aggregate and contextualize threat intelligence across sources for instant insight. Assess new vulnerabilities fast and resolve them quicker using past learnings.
GRC Teams
Automated control mapping, real-time compliance updates, and instant reporting. Identify gaps and continuously improve governance and procedures.
GRC Teams
Automated control mapping, real-time compliance updates, and instant reporting. Identify gaps and continuously improve governance and procedures.
GRC Teams
Automated control mapping, real-time compliance updates, and instant reporting. Identify gaps and continuously improve governance and procedures.
Threat Hunters
Predict and uncover hidden exploitable paths using advanced threat-hunting techniques. AI-powered Cyber Mesh and cross-tool intelligence enable proactive detection and remediation.
Threat Hunters
Predict and uncover hidden exploitable paths using advanced threat-hunting techniques. AI-powered Cyber Mesh and cross-tool intelligence enable proactive detection and remediation.
Threat Hunters
Predict and uncover hidden exploitable paths using advanced threat-hunting techniques. AI-powered Cyber Mesh and cross-tool intelligence enable proactive detection and remediation.
Incident Response
Incident Response Analysts benefit from rapid containment and response through low-code OOB integrations, a workflow editor, and agentic architecture—delivering optimized, AI-assisted remediation playbooks.
Incident Response
Incident Response Analysts benefit from rapid containment and response through low-code OOB integrations, a workflow editor, and agentic architecture—delivering optimized, AI-assisted remediation playbooks.
Incident Response
Incident Response Analysts benefit from rapid containment and response through low-code OOB integrations, a workflow editor, and agentic architecture—delivering optimized, AI-assisted remediation playbooks.

For Security Analysts
Where Analysts Gain the Upper Hand
MaayaAI delivers real-time intelligence, automated analysis, and predictive insights for security teams. Centralized dashboards and continuous monitoring help analysts respond faster and stay ahead of threats.

For Security Analysts
Where Analysts Gain the Upper Hand
MaayaAI delivers real-time intelligence, automated analysis, and predictive insights for security teams. Centralized dashboards and continuous monitoring help analysts respond faster and stay ahead of threats.

For Security Analysts
Where Analysts Gain the Upper Hand
MaayaAI delivers real-time intelligence, automated analysis, and predictive insights for security teams. Centralized dashboards and continuous monitoring help analysts respond faster and stay ahead of threats.
Power of the MaayaAI platform based on advanced AI technologies
Power of the MaayaAI platform based on advanced AI technologies


Hybrid RAGs/ Graph Neural Networks (GNNs) & Autoencoders (GAEs)


Hybrid RAGs/ Graph Neural Networks (GNNs) & Autoencoders (GAEs)


Hybrid RAGs/ Graph Neural Networks (GNNs) & Autoencoders (GAEs)


Specialized Language Models (SLMs)


Specialized Language Models (SLMs)


Specialized Language Models (SLMs)


Proprietary Security Knowledge Graphs (SKGs)


Proprietary Security Knowledge Graphs (SKGs)


Proprietary Security Knowledge Graphs (SKGs)
Rethink how you detect, respond, and secure —with precision at scale.
Rethink how you detect, respond, and secure —
with precision at scale.
MaayaAI unifies security tools and data into a single AI-native ecosystem, delivering complete visibility and control. Powered by proprietary hyper-tuned models, knowledge graphs, and GenAI agents, it automates triage, investigations, and response while enabling early threat detection and ASCA. The result is faster risk mitigation with reduced operational complexity and fragmentation.
MaayaAI unifies security tools and data into a single AI-native ecosystem, delivering complete visibility and control. Powered by proprietary hyper-tuned models, knowledge graphs, and GenAI agents, it automates triage, investigations, and response while enabling early threat detection and ASCA. The result is faster risk mitigation with reduced operational complexity and fragmentation.
Use Cases by Role
Use Cases by Role
Use Cases by Role
Designed for the Teams
on the Frontline
Designed for the Teams
on the Frontline
Purpose-built for DFIR, InfoSec, and Threat Hunting teams.
Autonomous AI that accelerates investigations and decisions.
Purpose-built for DFIR, InfoSec, and Threat Hunting teams. Autonomous AI that accelerates investigations and decisions.
DFIR Analyst
Rapid Incident Response, Early Threat Detection & Automated Forensics
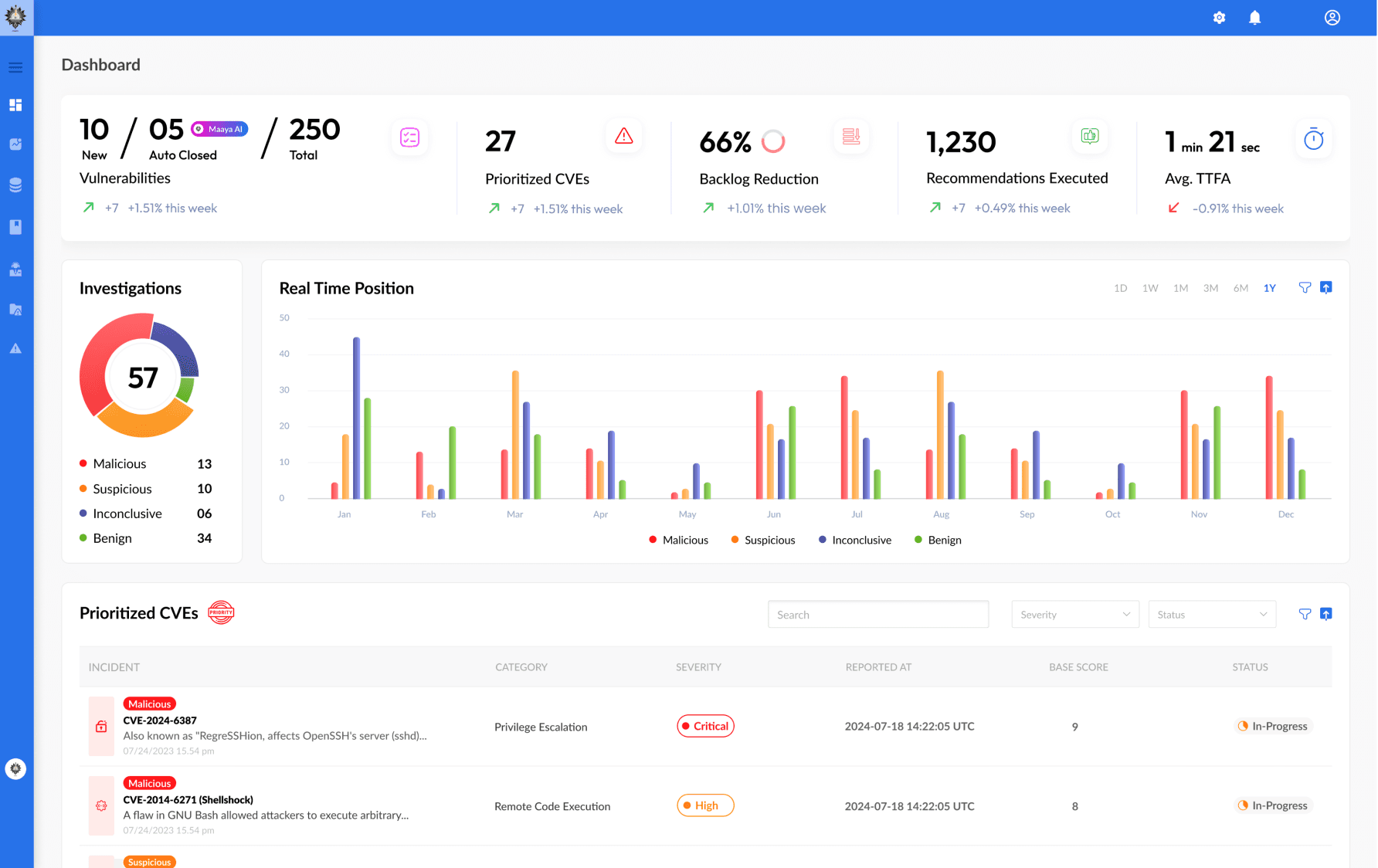
Autonomous and AI-Assisted Cyber Investigations
Comprehensive Log Analysis, Enrichment, and Correlation
Auto IOC Detection & Behavior Extraction
Contextualized Threat Intelligence for Actionable Insights
Purpose-Built, AI-Native Agents for Security Automation
End-to-End Forensic Analysis and Report Generation
DFIR Analyst
Rapid Incident Response, Early Threat Detection & Automated Forensics

Autonomous and AI-Assisted Cyber Investigations
Comprehensive Log Analysis, Enrichment, and Correlation
Auto IOC Detection & Behavior Extraction
Contextualized Threat Intelligence for Actionable Insights
Purpose-Built, AI-Native Agents for Security Automation
End-to-End Forensic Analysis and Report Generation
DFIR Analyst
Rapid Incident Response, Early Threat Detection & Automated Forensics

Autonomous and AI-Assisted Cyber Investigations
Comprehensive Log Analysis, Enrichment, and Correlation
Auto IOC Detection & Behavior Extraction
Contextualized Threat Intelligence for Actionable Insights
Purpose-Built, AI-Native Agents for Security Automation
End-to-End Forensic Analysis and Report Generation
Info Security Analyst
Instant Vulnerability, Impact and Automated Security Controls Assessment

Real-Time 0-Day Detection across all assets
Know the Impact Fast with blast radius–driven prioritization
Root Causes, Ready Fixes delivered in minutes
See the Unseen — Hidden Attack Paths & Exploitability
Always Contextualized with automated threat enrichment
Reports on Demand — clear, complete, and instant
Info Security Analyst
Instant Vulnerability, Impact and Automated Security Controls Assessment

Real-Time 0-Day Detection across all assets
Know the Impact Fast with blast radius–driven prioritization
Root Causes, Ready Fixes delivered in minutes
See the Unseen — Hidden Attack Paths & Exploitability
Always Contextualized with automated threat enrichment
Reports on Demand — clear, complete, and instant
Info Security Analyst
Instant Vulnerability, Impact and Automated Security Controls Assessment

Real-Time 0-Day Detection across all assets
Know the Impact Fast with blast radius–driven prioritization
Root Causes, Ready Fixes delivered in minutes
See the Unseen — Hidden Attack Paths & Exploitability
Always Contextualized with automated threat enrichment
Reports on Demand — clear, complete, and instant
Use Cases by Capability
Use Cases by Capability
Use Cases by Capability
From Detection to Resolution
From Detection to Resolution
AI-driven workflows that turn security signals into action.
Automated validation, response, and risk reduction at scale.
AI-driven workflows that turn security signals into action. Automated validation, response, and risk reduction at scale.
Automated Vulnerability Mapping & Threat Validation

MaayaAI ingests vulnerability data, validates threats, and analyzes attack paths using AI, transforming raw inputs into precise, context-rich insights that secure operations teams can act on—accelerating and improving vulnerability triage and risk comprehension.
Automated Vulnerability Mapping & Threat Validation

MaayaAI ingests vulnerability data, validates threats, and analyzes attack paths using AI, transforming raw inputs into precise, context-rich insights that secure operations teams can act on—accelerating and improving vulnerability triage and risk comprehension.
Automated Vulnerability Mapping & Threat Validation

MaayaAI ingests vulnerability data, validates threats, and analyzes attack paths using AI, transforming raw inputs into precise, context-rich insights that secure operations teams can act on—accelerating and improving vulnerability triage and risk comprehension.
Real-Time Response Enablement

MaayaAI links security gaps with live data for AI-driven automated responses. Its exploitability assessment identifies real threats, prioritizes precise remediation, and reduces noise and backlogs in minutes—empowering teams to act faster and stay agile.
Real-Time Response Enablement

MaayaAI links security gaps with live data for AI-driven automated responses. Its exploitability assessment identifies real threats, prioritizes precise remediation, and reduces noise and backlogs in minutes—empowering teams to act faster and stay agile.
Real-Time Response Enablement

MaayaAI links security gaps with live data for AI-driven automated responses. Its exploitability assessment identifies real threats, prioritizes precise remediation, and reduces noise and backlogs in minutes—empowering teams to act faster and stay agile.
Experience the future of cybersecurity with MaayaAI.
Experience the future of cybersecurity with MaayaAI.
Your transformation starts here
Your transformation starts here